PROTECT+ Head of Security Services, Kevin O’Sullivan, dives deep into Security Information and Event Management (SIEM) best practice considerations following a recent presentation to the Water Sector Association of Australia and the Institute of Water Administration Special Interest Group.
To find out more, including how PROTECT+ can work for your organisation, get in touch with our experts.
I was asked to present as part of the latest Water Services Association of Australia and the Institute of Water Administration Special Interest Group forums, with the subject being Security Information and Event Management (SIEM) best practice considerations.
Having worked in establishing security operations capabilities, which leverage SIEM platforms, over many years with very talented teams, the presentation allowed me to reflect and really think about what is it that makes a SIEM platform work, and whether organisations need a SIEM in the first place.
First things first: A SIEM platform is a data platform so your approach to data sets the foundation for successful SIEM practice.
SIEM in the market: There is a lot of choice
Before I get into the recommended considerations when looking at a SIEM investment, it is a good idea to look at what is happening in the market. Over the past 10 years, there have been significant developments in the technical capabilities of SIEM platforms across many providers.
Gartner’s analysis and magic quadrant is always a good place to look. What is interesting is that the competition is heating up with many of the traditional SIEM vendors being joined in the market by major cloud providers, next generation end point solutions, and the big data and analytics vendors.
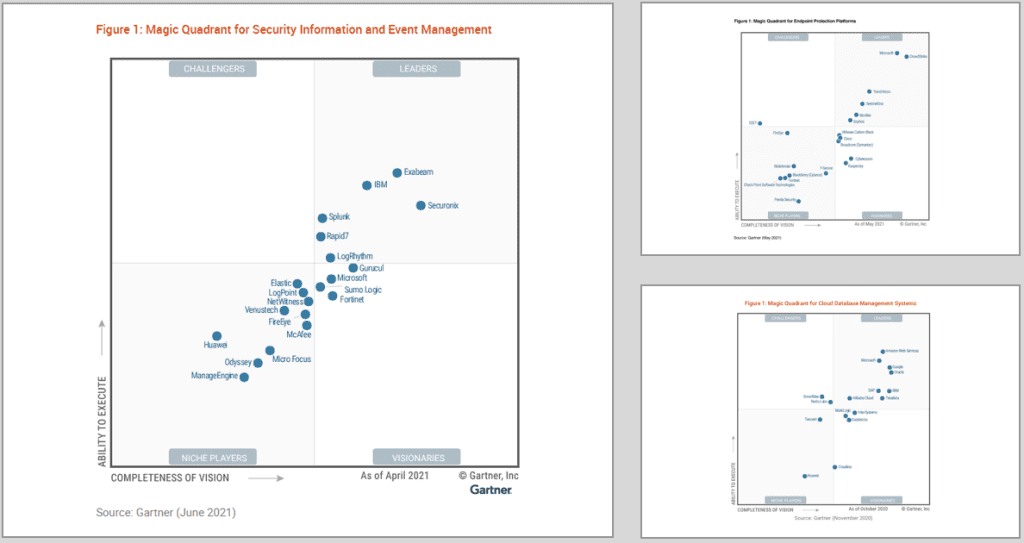
This really does allow for more choice but at the same time can make it a more difficult decision to make. There are so many new features and capabilities entering the market that you may ask yourself:
- Does our organisation need a SIEM?
- What is Extended Detection and Response (XDR) and does that replace my SIEM?
- Do I need a Security Orchestration, Automation and Response (SOAR) platform? Isn’t that my SIEM?
- Do I need a Security Operations Centre (SOC)?
Following this reflection, Gartner’s definitions of SIEM, SOAR, Data & Analytics and XDR are fairly similar and may be helpful to explore:
- SIEM “supports threat detection, compliance and security incident management through the collection and analysis of security events, as well as a wide variety of other event and contextual data sources”.
- SOAR enables “organisations to collect inputs monitored by the security operations team”.
- Data and analytics, to paraphrase, provide for the management of data for all uses (operational and analytical), and the analysis of data to drive business processes and improve business outcomes through more effective decision-making, and enhanced customer experiences.
- XDR is “a unified security incident detection and response platform that automatically collects and correlates data from multiple proprietary security components”.
Determining the differences among these options and figuring out which would best suit an organisation is a challenge for security teams to say the least, however there is a common element to them all which is data.
The guidance and considerations in this article are what we have learned over time and has fed into how Kinetic IT PROTECT+ teams establish our methodology and practice – not just with SIEM but our overall security operations.
What is ‘good practice’ SIEM?
I’ll take you through four areas that you may want to consider when investing in a SIEM and/or security operations capability. This applies equally if you or your organisation are looking to establish your own capabilities or looking to lean on your provider and partner networks.
As mentioned, your approach to data is the foundation which then needs to incorporate cyber security context, the skills and capability of your workforce and other external factors. The four SIEM considerations I will touch on in this insight include:
- Data Science Methodologies
- The Threat Intelligence Lifecycle
- Skills to support a modern SIEM environment and,
- The Funnel of Fidelity
1. Data Science Methodologies
The adoption of new technologies, the increase in flexible working, the ease with which our teams and customers have access to data has become our new normal. This has opened up so many opportunities for innovation and diverse ways of working which is fantastic. Yet, it has also increased our reliance on technology and the threat to information misuse, cyber-attack or breach.
Data and information is everywhere and all SIEM platforms consume it. So it is vital that you understand your data footprint and establish a program based on it.
The Cross Industry Standard Process for Data Mining (CRISP-DM) is a good approach for any organisation.
This is a process model with six phases which describe the data science lifecycle. Published in 1999 to standardise data mining processes across industries, it has since become the most common methodology for data mining, analytics, and data science projects.
Here’s a visual representation of this model that our PROTECT+ team promotes:
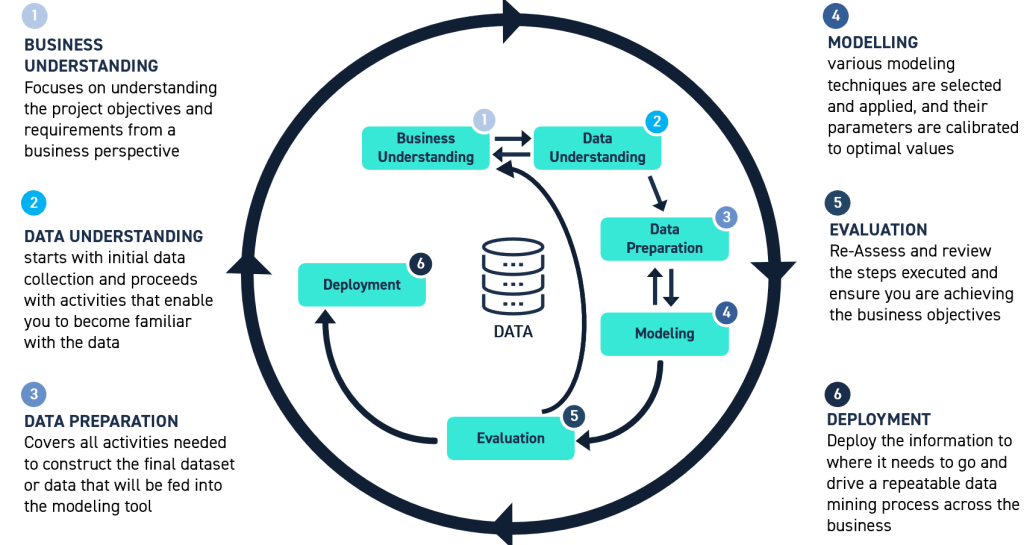
You can utilise the guiding principles of the CRISP-DM process and align these to your cyber security program and SIEM development.
2. The Threat Intelligence Lifecycle
Aligning your data program to your cyber security strategy is a very important consideration particularly when it comes to making the most out of your SIEM platform. Access to real time intelligence is the key here so your security operations teams are able to quickly investigate and respond to Indicators of Attack or Compromise.
Your approach to data and telemetry in the context of cyber security needs to be integrated closely with your security and risk management processes. Although a daunting task, the Threat Intelligence Lifecyle is a great way of breaking down the stages that need to be considered. Threat Intelligence is built on analytical techniques and, like CRISP-DM, the Threat Intelligence Lifecycle focuses on six phases: direction, collection, processing, analysis, dissemination and feedback.
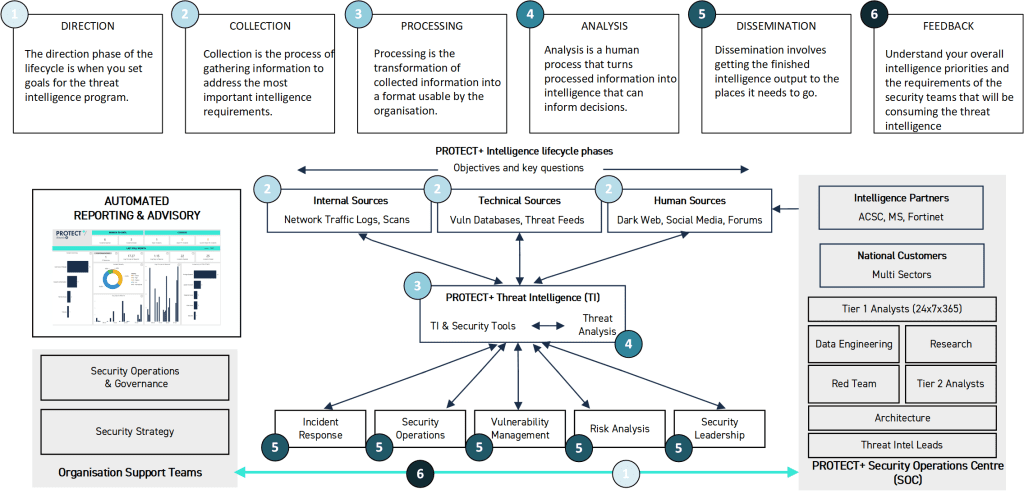
By going through the Threat Intelligence Lifecycle, organisations can begin to understand that there is more to SIEM best practice than just the platform and features alone. There is equally, if not more, important to ensure you have to right skills and capabilities – let’s call this human intelligence – to make your SIEM journey a success.
3. Skills to support a modern SIEM environment
Your SIEM is a data platform that supports multiple elements of your security operations through monitoring, response, investigation, forensics, risk, compliance – the list goes on. The SIEM is just one of many tools utilised by security operations teams and, as we all know, access to those with the right skills is becoming more and more competitive.
A critical component in your SIEM journey is identifying the current capabilities of your workforce – where you feel is best to invest and when is it best to engage with specialist partners and services providers. Cyber and information security is an extremely broad domain that requires a diverse range of skills and experience. Like data, this can be extremely daunting and may make you question, ‘where do I start?’
Once you have a better grasp on your approach to data and threat intelligence, you will be better placed to recognise what skills you have within your organisation and partner network, and where investment needs to be focused.
The National Initiative for Cybersecurity Education (NICE) and the Cyber Security Workforce Framework, that forms part of the NIST Special Publication 800-181, provide excellent guidance. Although US-based, the National Initiative for Cyber Security Careers and Studies has a great cyber career pathways tool that presents an interactive way to explore work roles within the NICE Workforce Framework for Cybersecurity.
It depicts the cyber workforce according to five distinct, yet complementary, skills communities. It also highlights core attributes among each of the 52 work roles, and offers actionable insights for employers, professionals and those considering a career in cyber.
4. The Funnel of Fidelity
There are many guiding principles that you can adopt when getting the most out of your SIEM and people investments; what we have highlighted in this insight are just a handful of them. These are good starting points, but you need to identify what works for your organisation and use the available frameworks as guides. It is important to also lean on your partner network.
The Kinetic IT PROTECT+ teams in our security operations have taken these guiding frameworks, and also adopted the principles within what is called the Funnel of Fidelity. This concept was first authored by Jared Atkinson from SpectorOPs and provides a simple model that we have tailored to incorporate other key elements of SIEM’s key features, as well as our security operations people capabilities. Here’s the PROTECT+ view:
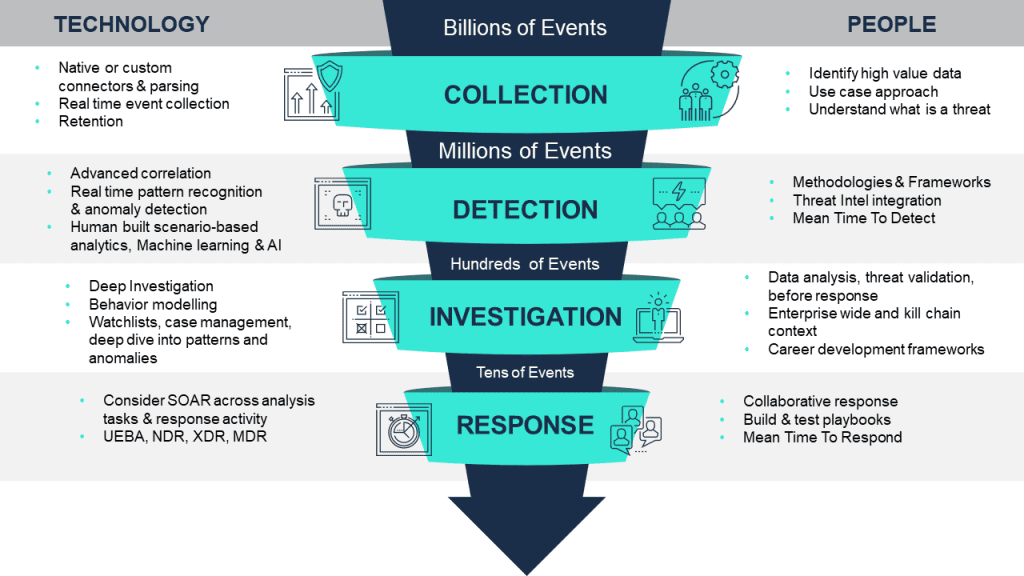
The Funnel of Fidelity is a model that contextualises the phases that must occur to successfully detect and remediate an attack. It depicts the process of applying different analytical procedures to manage millions of contextual events, and allows you to manage the level of resource (people) for investigative activities.
The top of the model has a greater reliance on SIEM capabilities and, as events pass through the model, the depth of analysis is increased leading to a shift in need for more specialist people capabilities.
It’s more than just the tools
SIEM platforms are an important tool for security operations teams, providing the foundation to increase visibility and an organisation’s ability to detect and respond to anomalous behaviour that may be an indicator of compromise or breach. SIEM capabilities continue to evolve and there is increased adoption of new innovative features which extend past automation and orchestration to real predictive capabilities, leveraging Machine Learning and Artificial Intelligence. SIEM best practice is more than just technology and the tool – it’s equally about your people and processes.
When looking to get the most of your investment in the technology ask yourself: Do I have the people to support it? What process do I need to adopt and change? Do I have relationships with the right vendors and partners? Answer these questions and your SIEM pathway will become a lot clearer and will support alignment to industry practice.
Kinetic IT and our PROTECT+ teams support Australian organisations across many industries and are more than happy to assist you in understanding your existing and future requirements, and ensure you are well placed to get return from your investments and increase your cyber resilience.
About Kevin O’Sullivan
Kevin O’Sullivan is the Head of Security Services for PROTECT+, a delivery arm of Kinetic IT which is Australia’s largest independently owned and operated provider specialising in managed ICT services, service integration and management, digital transformation and cyber security. For more than 10 years, Kevin has partnered with iconic Australian organisations to deliver seamless IT solutions and customer-centric outcomes, particularly in cyber security.
About PROTECT+
Kinetic IT’s PROTECT+ team delivers value-led, benefit driven security solutions tailored to fit your specific operational needs. Our knowledge of global security threats is backed by an unrivalled presence in the Australian IT landscape. Our specialist security crew are supported by a 1,400-strong team with intimate knowledge of customer operations.
Find out how PROTECT+ could work for your organisation.